CISCO (IOS) NAT / VPN Order of Operation

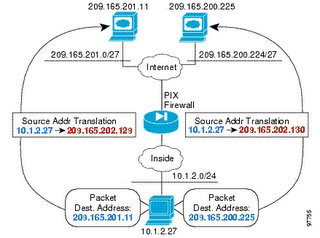
P.J. For the host on the 10.1.2.0/24 network accessing the two different servers, we have two ways to define the coonfiguration.
The syntax for using global translations follows:
access-list NET1 permit ip 10.1.2.0 255.255.255.0 209.165.201.0 255.255.255.224
access-list NET2 permit ip 10.1.2.0 255.255.255.0 209.165.200.224 255.255.255.224
nat (inside) 1 access-list NET1
global (outside) 1 209.165.202.129 255.255.255.255
nat (inside) 2 access-list NET2
global (outside) 2 209.165.202.130 255.255.255.255
The syntax for using static translations follows:
access-list NET1 permit ip host 10.1.2.27 209.165.201.0 255.255.255.224
access-list NET2 permit ip host 10.1.2.27 209.165.200.224 255.255.255.224
static (inside,outside) 209.165.202.129 access-list NET1
static (inside,outside) 209.165.202.130 access-list NET2
Limitations :
The following configuration limitations apply to policy NAT:
•Access lists must contain permit statements only. Access lists for policy NAT cannot contain deny statements.
•An access list must be used only once with the nat command. For example, the following configuration would produce an error:
nat (inside) 1 access-list mylist-A
nat (inside) 2 access-list mylist-A
Whereas, the following configuration would not produce an error:
nat (inside) 1 access-list mylist-A
nat (inside) 2 access-list mylist-B
•Use an access list only once between the nat and static commands.
•A global address cannot be used concurrently for NAT and PAT.
•static commands are matched and executed before nat commands.
•Policy NAT does not support SQL*Net, which is supported by regular NAT.